Checking your mailbox, uploading a document to Google Drive, or watching a film on Netflix—almost every action nowadays is linked to a cloud service. That is because companies are increasingly using cloud services such as web-based email, file storage, and SaaS to streamline operations and increase productivity. In 2025, it is even forecast that end-users worldwide will spend a total of $723.4 billion on public cloud services.
Unfortunately, the rise of cloud services also brings a pressing concern: cloud security. Companies are reporting more cloud security threats than ever before due to advanced cybercrime tools, the rise of AI, and weakened security barriers. As cybercrime becomes less complex and more accessible, cloud attacks in 2025 are expected to come not only from highly skilled hackers, but also from less skilled and newer actors.
What are the most common cloud security threats in 2025, and how can companies attract the right specialists to ensure cloud safety?
Why is Cloud Security Important?
Cloud services provide many advantages, but there are also concerns such as a lack of visibility, strict compliance requirements, and dependency on third-party providers.
If a company experiences a cloud security incident, this can have serious consequences, including:
• Financial losses
• Reputational damage
• Legal consequences and penalties
• Data loss and theft
• Business disruptions
• Loss of competitive advantage in the market
Cybersecurity Insiders revealed that 61% of surveyed organisations reported breaches last year. As a result, 63% plan to increase their cloud security budget in the next 12 months. As companies become increasingly dependent on cloud services, strong cloud security is not a luxury, but a necessity.
Most Common Cloud Security Incidents
In conclusion, cloud security is not just a protective measure but also a strategic investment that ensures a company’s long-term sustainability, safety, and growth.
So, what are the most common cloud security incidents? According to a study by Cybersecurity Insiders:
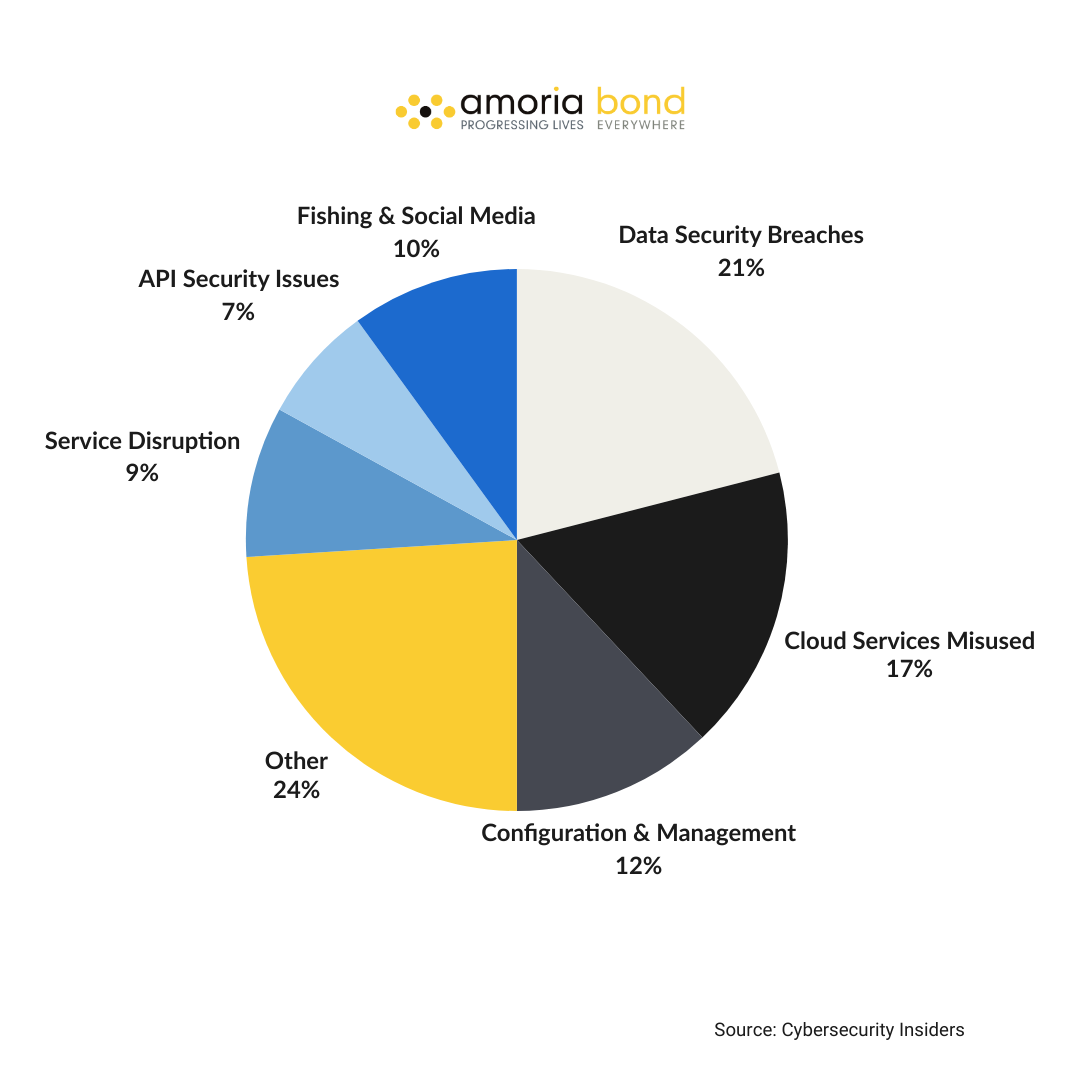
The most frequently reported cloud security incidents were data security breaches followed by cloud services being misused and configuration & management. Other cloud security incidents were supply chain attacks (6%), malware-related incidents (5%), user activity related (3%), compliance violations (3%), software vulnerabilities (3%) and other (4%).
API Vulnerabilities
API security issues are among the most common cloud attack vectors for companies. Attackers can exploit weaknesses and security gaps, such as weak authentication, outdated software, and vulnerabilities in APIs, to gain unauthorised access, steal data, or disrupt services.
Securing APIs is crucial for cloud services because they act as the bridge between different cloud applications, services, and users. Companies can enhance API security by implementing rate limiting and throttling measures to protect cloud tools against attacks such as DoS. Other essential security measures include ensuring product parity, performing regular security control updates, and automating credential management.
Data Breaches
A data breach is not an uncommon concept in cloud security. Even major companies like Facebook, LinkedIn, and Adobe have experienced data breaches in recent years, exposing sensitive user information.
Besides legal consequences and reputational damage, companies face severe financial losses. The average cost of a data breach in 2024 was $4.88 million, representing a 10% increase compared to the previous year.
Companies can enhance their cloud security against data breaches by implementing Multi-Factor Authentication (MFA), the Principle of Least Privilege (PoLP), regular security audits and cloud-native security tools.
Misuse of Cloud Services
Cybercriminals can exploit cloud services for fraudulent and illegal activities. For example, attackers can launch host-based attacks, such as Command & Control (C2) Servers and DDoS attacks, or an employee may upload confidential documents before leaving the company.
Monitoring cloud activity, enforcing strong access control such as Multi-Factor Authentication (MFA), and conducting regular security audits are effective tactics to reduce the risk of cloud service misuse. Additionally, providing employee training on how to use—and more importantly, how not to use—the cloud is crucial for preventing data breaches and unauthorised access.
Configuration and Management
Having a strong foundation is the most important part of building a house, and the same principle applies to the cloud. Misconfiguration and mismanagement of cloud services are often the result of human error, a lack of security policies, or failure to follow best practices.
Unsecured cloud storage, a lack of data encryption, and leaving default security settings enabled make cloud services vulnerable to cyberattacks. Additionally, mismanagement, such as poor cost management and inadequate backup strategies, can cause serious damage to a company’s security posture.
Due to the complexity of cloud environments, minimising human error can be challenging for IT experts. However, companies can take several preventative measures, such as implementing automated remediation solutions and configuration checks, which increase efficiency and reduce manual workload. To prevent mismanagement, organisations should conduct security awareness training and apply the Principle of Least Privilege (PoLP).
Phishing and Social Media
Phishing and social media-related cloud incidents are a growing threat. According to Statista, the most common security attack in both cloud and on-premises environments worldwide in 2024 was phishing, with over 70% of respondents reporting that their company had experienced this type of attack.
Some common examples include credential harvesting, malicious ads, and cloud subscription scams.
To mitigate the risk of phishing and social media-related incidents, companies should monitor social media for fake accounts, use email security tools, and enable Multi-Factor Authentication (MFA).

Service Disruption
Service disruptions have a severe impact on the daily operations of many companies, which only highlights the importance of cloud security. In 2024, Microsoft and AWS experienced outages for several hours due to a cyberattack. The average cost of downtime can be as high as $9,000 per minute. A service disruption in higher-risk sectors like finance and healthcare can, in some cases, cost $5 million per hour.
Using hybrid and multi-cloud strategies decreases dependence on a specific cloud provider and reduces damage when a service disruption occurs. Other security measures companies can take include implementing disaster recovery plans and monitoring cloud services to detect security threats and performance degradation.
Working with a Specialised IT Recruitment Organisation
A key obstacle for companies in ensuring cloud security is the lack of expertise. In the Cybersecurity Insiders' cloud security report, 41% of organisations stated that the lack of security awareness among employees was a barrier to adequately defending the company against cyberattacks. For 38%, the barrier was rapid technological changes, and for 37% of companies, the biggest barrier to cloud security was the lack of skilled personnel.
Having the right expertise in cloud security is essential to mitigate these threats. The same Cybersecurity Insiders report revealed that 76% of respondents reported a shortage of skilled cybersecurity professionals.
Working with a specialised technology recruitment organisation can be a solution to staff shortages in cybersecurity. These organisations understand the sector and can tap into an extensive candidate pool. Furthermore, companies can reduce costs by working with a recruitment organisation, as employers can reallocate HR costs to other projects and growth opportunities.
Does your company face a staff shortage in cloud security, or are you planning a cloud security project? Contact me or my team to discuss how Amoria Bond can support your staffing goals.






